Designer
SECURing THE
space internet
space internet
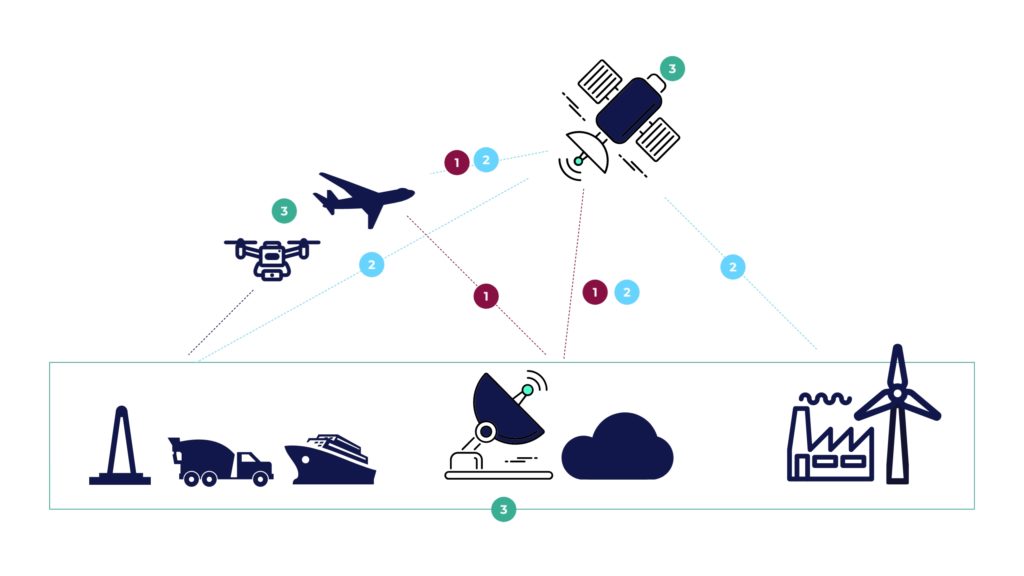
CYSEC provides world-leading, high-performance cybersecurity tools to ensure robustness, confidentiality, and integrity for the space internet networks & critical infrastructures.
Starlink
ARCA SATCOM
VPN
Enhance your Starlink network
with unmatched performance
and quality with ARCA SATCOM
with unmatched performance
and quality with ARCA SATCOM
Arca Trusted OS
ARCA Trusted OS
Arca Trusted OS is a hardened Linux-based operating system combined with a secure Kubernetes orchestrator to provide a trusted runtime platform for containers.

CYSAT

Organized by CYSEC
The biggest European event entirely dedicated to
Cybersecurity for
the space industry
May 14-15, 2025 - Paris, Station F