Sovereign clouds adoption is getting popular due to growing demands for data sovereignty, regulatory compliance, and enhanced security. They ensure sensitive data stays within national boundaries, adhering to local laws while mitigating risks from foreign jurisdiction. Critical industries, public trust, and government mandates further drive their adoption, supporting digital independence and innovation.
Various approaches, various regulations, various offers are pupping up into the sovereign cloud markets. Although some initiatives like the European Cybersecurity Certification Scheme for Cloud Services (EUCS) that aims to unify existing regulations across EU member states, the actual situation is that companies face a patchwork of sovereignty cloud services that come with different levels of trust. These different levels of trusts are not always well perceived by the buyers, often more preoccupied by the growing number of regulations they have to comply with like the GDPR or the Digital Operational Resilience Act (DORA).
Sovereign cloud trust levels range from basic data residency, ensuring data stays within specific geographic boundaries, to full national or strategic trust, aligning with a nation’s digital sovereignty goals. Key levels include data sovereignty (protection from foreign jurisdiction), operational sovereignty (local management and support), control and access trust (customer-controlled encryption and access), compliance trust (certifications for regulatory standards), and technological sovereignty (use of open-source or local technologies). These levels address varying needs for security, compliance, and control, enabling organizations and governments to choose solutions aligned with their operational, regulatory, and strategic priorities.
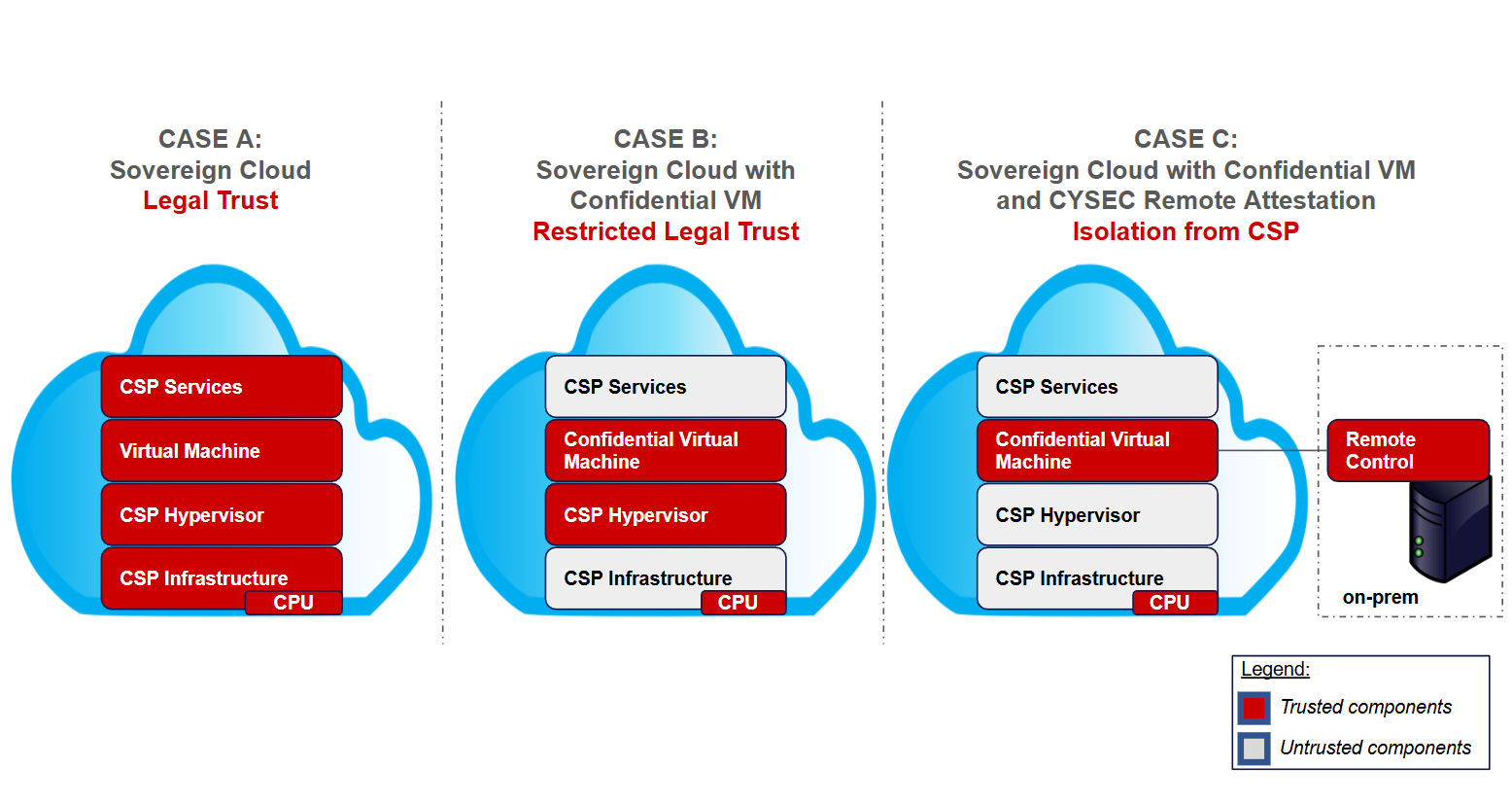
In a schematic way, we consider three cases that explain how the different level of trust towards CSP can be enforced with a brief representation described in the figure below.
Schematic representation of three cases of level of trust in sovereign cloud
- CASE A: Companies can rely on the legal terms that will regulate the service subscribed and/or introduce technologies that guarantee a higher level of isolation and control on the environment used within the third party infrastructure (ex. CSP). Many countries in Europe see the rise of local sovereign cloud offerings like Bleu, Sense, OVH but as well as from the hyperscalers like AWS in Germany or Azure in China, US and Germany. The trust is regulated by legal agreements between both parties.
- CASE B: With the arrival of confidential computing technologies (see blog on Confidential Computing), some CSPs have introduced Confidential VM instances. These instances use hardware-based memory encryption to help ensure your data and applications can’t be read or modified while in use. Confidential VM instances offer a mechanism of VM isolation and a mechanism of attestation. This isolation is hardware-based and cryptographic. It isolates a VM from the other processes and tenants of the cloud (including the cloud host). The attestation mechanism is provided by a secure processor in the CPU and operated by the CSP. Attestation allows the VM owner to verify the identity and the state of the VM based on attestation reports generated by the CPU. Meanwhile this is a significant progress, companies still need to trust the CSP as it operates the attestation mechanism. Trusting the legal part still remains although in much narrower terms thanks to the level of control provided by the confidential VM instances .
- CASE C: In order to remove the necessary remaining trust given to the CSP, an innovative approach is proposed by CYSEC to create an on-prem attestation service operated by the VM owner that give the full control to the owner of the Confidential VM to remotely verify the proper setup of the CC context and the integrity of its system during the launch of its VM. Coupled with an encryption key storage such as an HSM (Hardware security Module), the owner of the VM ensures a complete isolation of its data, applications and IP when stored or used within the cloud provider environment. To know more about CYSEC Remote Control check this blog Remote Control).
The essence of the CYSEC solution that combined a hardened operating system as a guest OS within the confidential VM and an on-prem attestation verification manager to use the remote control mechanism has been specifically designed to help companies looking to leverage cloud agility and scalability meanwhile refusing any compromise on data sovereignty. It delivers a Trusted Execution Environment for containers that contains attack propagation in container clusters and avoids corruption of container data and provides the protection of data in all states: at-rest, in transit, and in-use.
Security and defence bodies, industrial and healthcare players or financial institutions can leverage such a solution to protect their sensitive data, business applications, AI solutions or facilitate industry vertical compliance in cloud environments.