Edge computing enables companies to offer faster, more responsive services compared to competitors relying solely on centralized cloud architectures. It is also one of the major sources of data to fulfill big data lakes and enrich AI modeling. The continuous emergence of pervasive networking technology, ubiquitous computing coupled with the desire to support user mobility, the increasing demand of advanced services (ex. AI) and the view of distributed systems as a utility accelerate the demand for edge computing architectures.
The deployment of a distributed system such as edge computing can be expensive to acquire, install, maintain, and upgrade, especially for large or complex international deployment. Such solutions can produce a large amount of data that can be useful for decision making, performance evaluation, and optimization. However, this data also needs to be collected, stored, analyzed, and presented in a meaningful and actionable way. The nature of edge computing can expose the operations to various cyber threats, such as hacking, malware, or data breaches, that can compromise the integrity, confidentiality, and availability of the data and devices. Finally, in order to remain competitive and relevant, companies cannot rely on a one-time investment or a static solution but on adaptive solutions enabling continuous process of learning, experimenting, and improving. One of the technologies supporting these business needs is the containerization of services and applications.
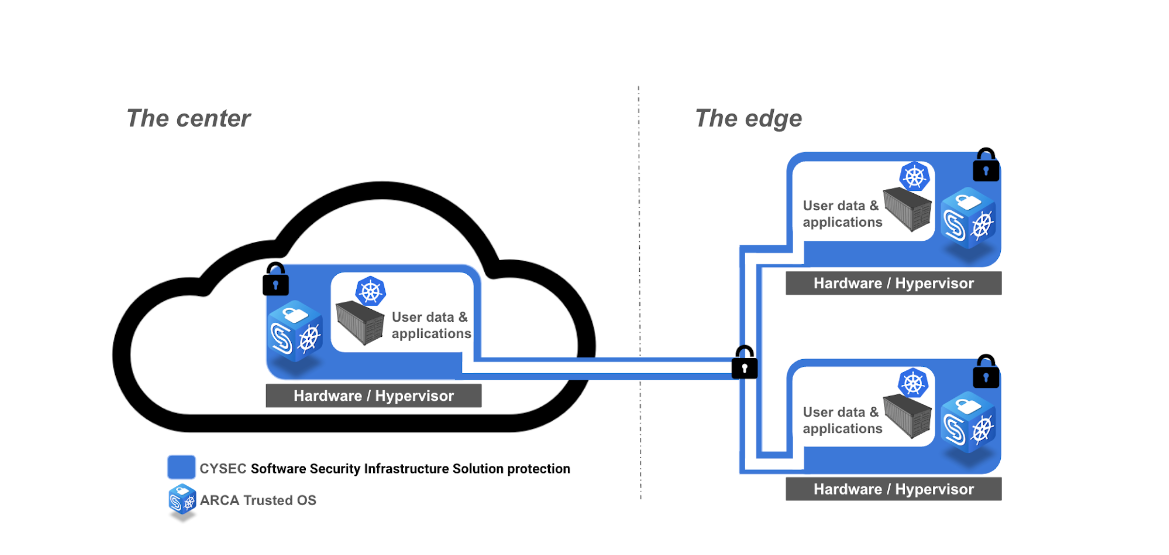
Building a complete edge computing solution can be pretty complex and the choice of the applications, tools and hardware must be triggered by the business purpose. In this context, CYSEC Software Security Infrastructure Solution has been designed to support companies looking to protect their fleet of distributed systems against unauthorized access to the infrastructure hosting edge system and to ensure the integrity of their running environments and the confidentiality of their data whatever they are at rest, in transit or in execution. It integrates remote capabilities for update/upgrade and supports edge solutions scalability without impacting the container DevOps activities. At the heart of CYSEC Software Security Infrastructure Solution, there is a hardened Linux-based micro distribution operating system called ARCA Trusted OS designed to only execute containerized applications that enables the creation of an envelope of protection of the execution environments and their data whatever they are collated in the cloud or at the edge (see figure below).