Cloud-based AI offers numerous benefits, but poses significant data privacy and security risks, especially for regulated organizations. CYSEC’s solution addresses these risks in two use-cases by isolating AI models and data within encrypted VMs in cloud environments. This protects data at rest, in transit, and in use, whether organizations deploy their own models or utilize third-party AI services. CYSEC’s Remote Control feature further enables independent verification of this isolation, ensuring data protection without cloud provider reliance.
Artificial intelligence (AI) offers organizations a wealth of potential benefits, from automating routine tasks and boosting efficiency to generating valuable insights from vast datasets and driving innovation. However, alongside these advantages, AI also presents significant risks. These include for example the potential for algorithmic bias, leading to unfair or discriminatory outcomes; the challenge of ensuring data privacy and security, especially with sensitive information; the difficulty in explaining and interpreting complex AI models (the “black box” problem), and hindering accountability and trust.
CYSEC addresses the risk of data privacy and security while organizations run their AI-based processes outside their premises Some organizations choose to run AI models outside their premises primarily for scalability and flexibility, leveraging cloud platforms’ on-demand access to vast computing resources and specialized hardware. This approach offers cost-effectiveness by avoiding large capital expenditures and paying only for resources used, accelerating deployment through pre-configured environments and tools. Outsourcing AI infrastructure also grants access to managed AI services, frees internal IT teams to focus on core business, enables global accessibility, and provides robust disaster recovery.
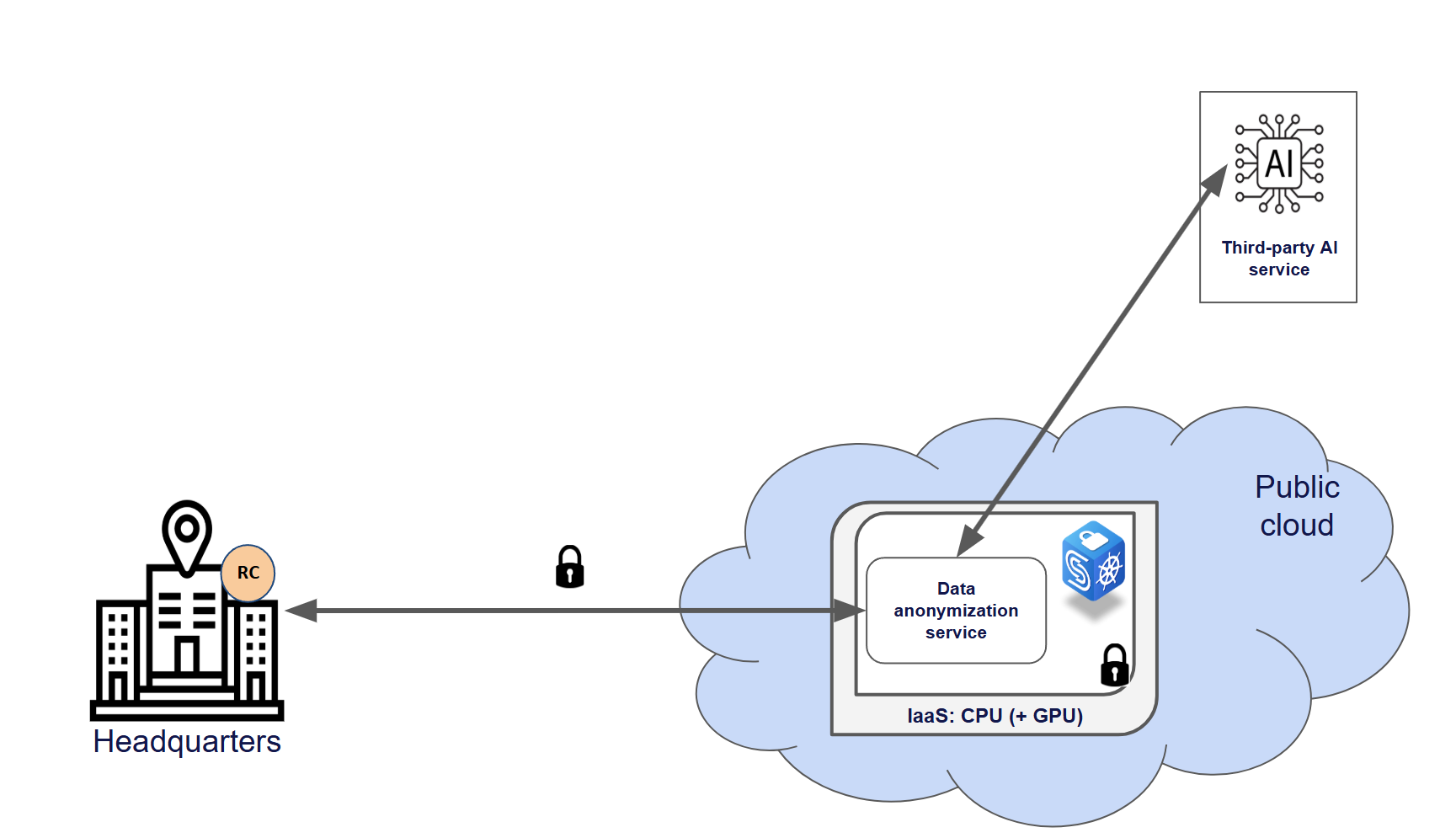
Nevertheless, regulated organizations should approach such infrastructure outsourcing with caution. Consider, for example, the online support service of a financial institution or telecommunications company. When such a service is provided by an on-site team, customer data privacy is relatively straightforward to manage, as the team operates within the organization’s secure premises. However, if the online service relies on an AI model running in a third-party cloud, the organization remains responsible for customer data privacy within that remote environment. CYSEC offers a solution that isolates the AI model and the processed customer data from other cloud processes by encrypting data in all states (at rest, in transit and in-use) within remote virtualized environments. Further details about this isolation solution are available in this blog post.
How does it work when you use your AI model?
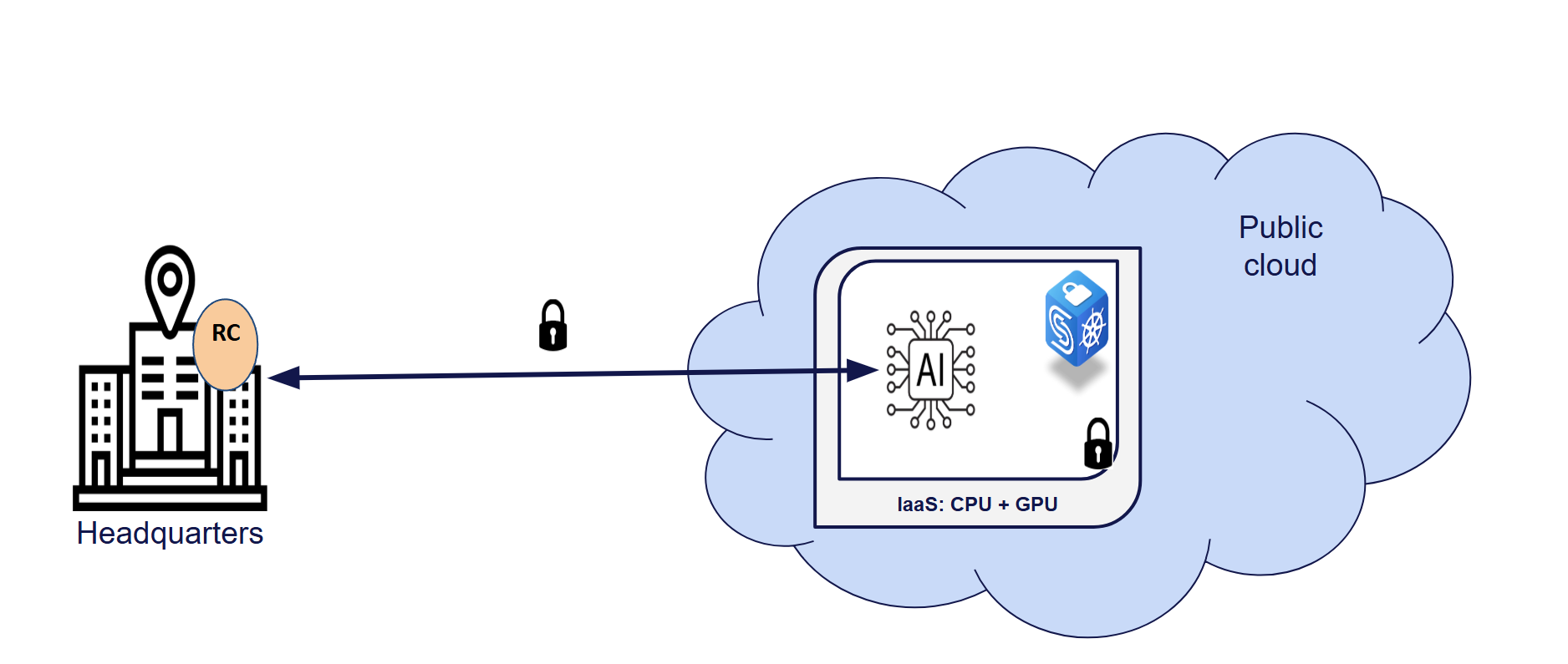
Some organizations choose to develop, train, and fine-tune their own AI models. In these cases, the solution depicted below can be used for the training, fine-tuning, and inference phases. Others opt to purchase pre-trained AI models from independent software vendors (ISVs) and deploy them on their preferred infrastructure for ease of use. Regardless of the approach, protecting these AI models and the data they process in third-party clouds requires a level of isolation that prevents any compromise to the confidentiality and integrity of this data—whether in transit, at rest, or in use. CYSEC’s solution provides such isolation for virtual machines (VMs) in (public or private) cloud environments. These VMs can utilize cloud computing resources without exposing data in clear text to other cloud tenants, including the cloud provider. With this architecture, AI models are simply deployed within these isolated VMs running in third-party clouds. Furthermore, CYSEC’s solution offers a feature called Remote Control (RC) that allows organizations to collect evidence directly from the CPU, verifying the isolation of the VMs without relying on the cloud provider. This enables independent monitoring of the isolation’s effectiveness.